Unless you have been living under a rock for the past 24 hours, you’ve heard all about the ongoing CIA / WikiLeaks fiasco. However, you’ve probably missed one positive takeaway that seems to have gone unnoticed by the majority of those following this story – i.e. a closer examination of the leak reveals indicators of strong collaboration and frequent information sharing with other intelligence agencies (e.g. FBI, NSA, etc.), as well as with agencies across the pond (e.g. MI5, GCHQ), other major security contractors (e.g. Raytheon), and even underground dark web sources.
Important, Because the Status Wasn't Always ‘Quo’
Sure, there are many negative implications and observations being made about this leak by the majority of cybersecurity pundits out there. Clearly this is embarrassing for the CIA to say the least. It also confirms a long-held suspicion and fear that our TVs would one day be capable of turning the tables and watching us back. But that said, it’s important to recognize the trend and not minimize the importance of fact that our intelligence agencies are working together and sharing threat intel effectively – a scenario that definitely has not always been the status quo.
In the aftermath of the 9/11 attacks, the CIA and other intelligence agencies were chastised for being disorganized and not effectively sharing threat intel amongst one another. Going forward, all were in agreement that steps would need to be taken to break down these silos, build effective communication paths between the CIA, NSA, FBI, DHS, and others within the security intelligence family tree.
“The Sept. 11 attacks were preventable, but the plot went undetected because of communications lapses between the F.B.I. and C.I.A., which failed to share intelligence related to two hijackers, a Congressional report to be released on Thursday says.”
Source: The New York Times - 9/11 Congressional Report Faults F.B.I.- C.I.A. Lapses - 24July2003
Stop, Collaborate and Listen. The CIA is Back With a Brand New Convention …
Now fast forward to March 2017 and the recent CIA leak. If we take a closer look at the posted CIA internal wiki pages available on WikiLeaks, you’ll notice that the CIA has been collaborating more closely and sharing intel with other intelligence agencies (e.g. NSA, FBI, GCHQ, MI5, etc.). Two concrete examples of this revealed in the leaks are: 1) sharing bought 0-day exploits and 2) hosting interdepartmental security lunch-n-learn sessions.
1. Zero-Day Exploit Sharing: Teamwork Makes the Dream Work
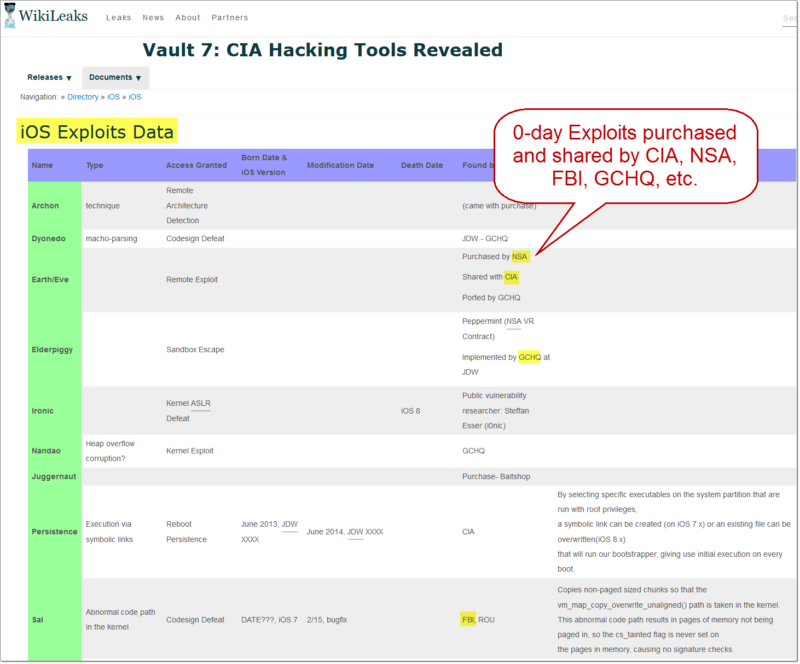
The CIA is clearly coordinating with other entities to share exploit development. This is evidenced by the capabilities matrices listed in the leaks that attribute the source of the exploits. Consider the iOS exploits page here:
iOS Exploits: https://wikileaks.org/ciav7p1/cms/page_13205587.html
This page attributes exploits found by the CIA itself, NSA, FBI, and even from some joint efforts with our intelligence agency friends from across the pond: GCHQ (British Intelligence) and MI5 (more British Intelligence). Other exploits are shared from independent researchers, third-party exploit development shops like Baitshop, and undisclosed black market purchases.
“The attack against Samsung smart TVs was developed in cooperation with the United Kingdom’s MI5/BTSS. After infestation, Weeping Angel places the target TV in a ‘Fake-Off’ mode, so that the owner falsely believes the TV is off when it is on. In ‘Fake-Off’ mode the TV operates as a bug, recording conversations in the room and sending them over the Internet to a covert CIA server.”
Source: Wikileaks.org - Vault 7 - Weeping Angel (Extending) Engineering Notes
2. Lunch-n-Learns: Intelligence Family Get Togethers
Past Presentations: https://wikileaks.org/ciav7p1/cms/page_9535799.html
Another example of evidence that the CIA is regularly collaborating and sharing intel with other agencies is from their lunch-n-learn past agendas page found in the leak. Specifically, "NERDS," which stands for Networking, Engineering, Research, and Development Symposium, is the CIA's regular series of brown-bag presentations on technical subjects (e.g. usually on how to hack into various kinds of technologies).
The schedule of events clearly shows a wide array of interdepartmental (and inter-organizational) cooperation:
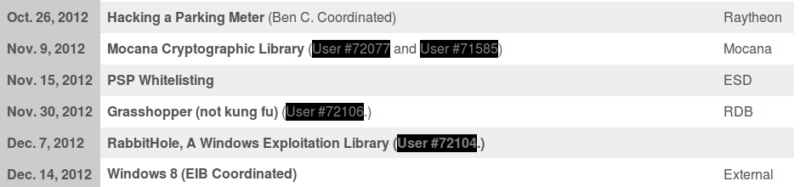
Above you can see groups Raytheon (the DoD contractor), Mocana (a startup in San Francisco) on the list of brown-bag presenters.
Other examples on this list include MITRE (The DoD contractor and research farm), Pikewerks (a cybersecurity company acquired by Raytheon), and the NSA.
In Conclusion: Look On The Bright Side of Spies
It’ll be interesting to see how these next few weeks play out, but aside from some fluky mentions of a push-up tracker and authorized emoji libraries, don’t get lost in the hype. There is a bright side to strife – and that includes massive leaks of internal CIA information.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.