Border Gateway Protocol (BGP) is a crucial component of the Internet, responsible for determining routing paths. BGP hijacking — that is, using BGP to manipulate Internet routing paths — has become more frequent in recent years. Cybercriminals and governments alike have taken advantage of this technique for their own ends, such as traffic misdirection and interception. This blog post will provide an overview to BGP and describe how BGP hijacking is performed.
Introduction to BGP
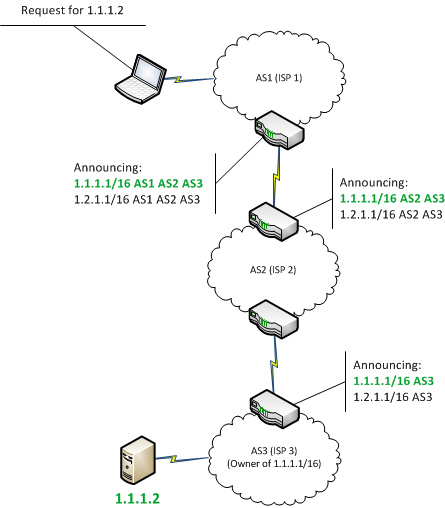
BGP is a protocol used to exchange routing information between networks on the Internet. It is used to determine the most efficient way to route data between independently operated networks, or Autonomous Systems. As such, BGP is commonly used to find a path to route data from ISP to ISP. It is important to note that BGP is not used to transfer data, but rather to determine the most efficient routing path. The actual transfer is accomplished using whatever protocol is necessary, likely another member of the TCP/IP suite.
In technical terms, a collection of IP prefixes operated by the same entity is referred to as an Autonomous System. Autonomous Systems are each assigned an Autonomous System Number (ASN) by the Internet Assigned Numbers Authority (IANA). Let’s demonstrate:
Here in Phoenix, I’m currently assigned an IP address from my ISP, Cox Communications — assume this is 70.177.9.30. This IP address belongs to the larger address space, 70.177.0.0/20, referred to as a prefix. The 70.177.0.0/20 prefix is owned by Cox Communications, and is announced as part of AS22773. AS22773 announces hundreds of prefixes, of which 70.177.0.0/20 is a part.
Now, assume I need to send data to the other side of the world. Eventually this data must leave the network my ISP controls, and BGP must be used. Of course, a routing path can’t be determined from one Autonomous System alone. This is where BGP peers, or neighbors, come in. Peers are Autonomous Systems that have been manually configured to share routing data. As an Autonomous System “learns” new routes, this information is propagated to its peers. By aggregating routing information received from BGP peers, the router handling the data can identify the most efficient path. This path is determined by a variety of factors, including distance and configuration settings implemented by the router administrator. Because peers, and therefore route propagation, are manually configured, it is necessary to compromise an edge router broadcasting external BGP announcements to perform Internet-level BGP hijacking. Despite this difficulty, BGP hijacking attacks are occurring in the wild. Please refer to Figure I below for a graphical overview of BGP.
BGP Hijacking
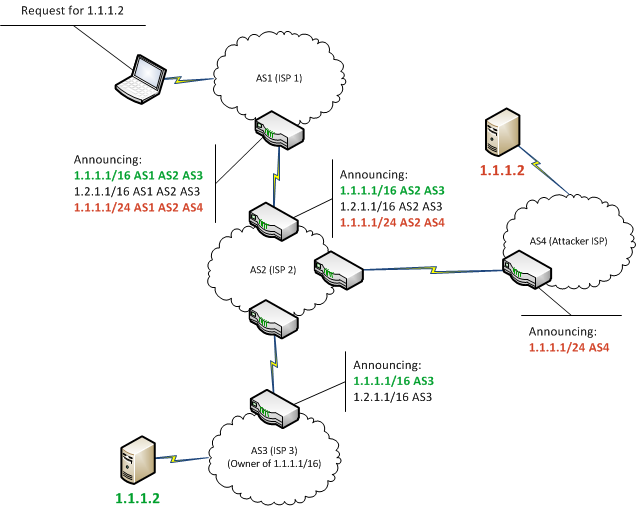
Since BGP determines how data travels from its source to its destination, security is a concern. By manipulating BGP, data can be rerouted in an attacker’s favor allowing them to intercept or modify traffic. Internet-level BGP hijacking is performed by configuring an edge router to announce prefixes that have not been assigned to it. If the malicious announcement is more specific than the legitimate one, or claims to offer a shorter path, the traffic may be directed to the attacker. Attackers will frequently target unused prefixes for hijacking to avoid attention from the legitimate owner. By broadcasting false prefix announcements, the compromised router may poison the Routing Information Base (RIB) of its peers, as shown in Figure II. After poisoning one peer, the malicious routing information could propagate to other peers, to other Autonomous Systems, and onto the broader Internet.
Multiple instances of BGP hijacking have been recorded in the last three years. In several examples documented by Renesys, BGP hijacking was performed in 2013 to reroute data through arbitrary countries prior to the intended destination. One attack saw traffic, intended to go from Mexico to the United States, diverted to Belarus before reaching its destination. By advertising false BGP broadcasts, the Belarusian ISP successfully propagated illegitimate routes onto the Internet. In this case, corporate or state espionage is a likely explanation. However, there are indications of BGP hijacking being performed by non-state adversaries as well.
In a 2014 attack analyzed by Dell SecureWorks, BGP hijacking was used to intercept Bitcoin miners’ connections to a mining pool server. By rerouting traffic to a mining pool controlled by the attackers, it was possible to steal the cryptocurrency resulting from the victim’s mining. This attack collected an estimated $83,000 in cryptocurrency over a two-month period.
In July 2015, a breach of the surveillance software provider Hacking Team resulted in a leak of internal company emails. The emails revealed that, in 2013, the Italian government worked with Hacking Team and an Italian ISP to conduct BGP hijacking. After an IP block hosting a Hacking Team command and control (C&C) server went offline, the malware communicating with the C&C was also left unreachable. By fraudulently announcing the IP prefix hosting the C&C, Hacking Team reestablished access with the infected machines. This is the first documented instance of a Western government using BGP hijacking.
Future Enhancements to BGP
As of this post’s publication, BGP hijacking is difficult to prevent, largely due to the design of BGP itself. The protocol does not support the ability to verify the accuracy of routing information. Perhaps the most promising improvement to BGP comes from the Internet Engineering Task Force (IETF) in the form of BGPsec. Like DNSsec, BGPsec is an extension to BGP that introduces several new protections. Among them is Resource Public Key Infrastructure (RPKI), which will provide a way to associate Autonomous Systems with cryptographic certificates to maintain integrity. Each AS will maintain a digitally signed Route Origination Authorization (ROA) that lists IP prefixes and which AS are permitted to announce them. The implementation of a RPKI for BGP would be a significant improvement to the protocol’s security.
Conclusion
Internet-level BGP hijacking is difficult to execute, since it requires access to edge routers. An attacker would likely need to compromise an ISP, or have an accomplice employed there. Difficulty in exploitation could explain why BGP hijacking attacks have received little attention and why there is no reliable method for preventing them yet. With that in mind, BGP hijacking attacks can be expected to continue.
Zach Julian presented on censorship detection through analysis of BGP data at Converge Detroit in July 2015.
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.