
NOTE: There is no conflict of interest in the following content. The products in this VPN guide were chosen strictly as a result of research. We received no compensation from any of the creators of our recommended VPNs.
Table of Contents
- Introduction
- Top 5 VPN Choices
- Methodology
- Other VPNS We Tested
Introduction
If you’re interested in installing and using a VPN to surf the internet securely, realize that not all VPNs are created equally. Some VPNs serve different purposes than others in terms of privacy, performance, and ease of use.
Before immediately jumping into our VPN guide, keep in mind this “caveat emptor” about free VPNs. Free VPNs are not free just because the creators believe that every person should have a VPN. Free VPNs have a history of doing some shady things.
Our Top 5 VPN Choices
When we began, we set out to rank VPN services and recommend the best. But during our testing, we discovered that each VPN had their strengths as well as weaknesses, making the idea of ranking “a best VPN” a little irrelevant. So without further ado, in no specific order or rank, here are our VPN choices based on your particular situation.
If you're interested in more detail, you can download this chart of all the VPNs we tested. [download id="6456"]

ExpressVPN
BOTTOM LINE: ExpressVPN has several solid features packed into an intuitive UI. Coupled with their widespread compatibility and fantastic online support, it’s a great choice for anyone willing to pay a little extra for some peace of mind.
Pros:
- Easy-to-use UI (user interface)
- Contains important features like an internet kill switch (terminates all network connections if VPN access is lost to avoid insecure data leaks) and secure DNS connection, all enabled by default
- Exceptional customer support, uses LiveChat
- Compatible with almost all major devices, such as Windows, Mac, iOS, Android, Linux, Kindle, as well as routers and manual configurations for much more
Cons:
- Slightly more expensive than most other VPNs, coming in at $12.95 a month
- Limited to three concurrent connections across devices

PureVPN
BOTTOM LINE: PureVPN has the best download and upload speeds of the VPNs we tested by a large margin. Users who are more technically adept will find PureVPN their best option and gravitate toward features like split tunneling.
Pros:
- Best speed performance in our testing environment!
- Feature-rich with an internet kill switch and secure DNS connection, as well as split tunneling and hotspot (Split tunneling allows users to choose what programs route traffic through the VPN, giving the ones that don’t uninhibited speed)
- Exceptional customer support, uses LiveChat
Cons:
- UI is difficult to navigate
- Insecure settings set by default
- Limited to three concurrent connections across devices

TorGuard
BOTTOM LINE: TorGuard places as much power in the user’s hands as possible. Protocol and cipher choices are on the main screen, and users can write scripts that execute before and after VPN connections. TorGuard is an excellent choice for users with a thorough understanding of encryption and network traffic.
Pros:
- Heavy customization available with scripts and settings changes
- Variety of features, such as an internet kill switch, secure DNS connection, and App kill
- Very few settings restrictions made for the sake of clarity, meaning less limitations on the user
- Great support, has LiveChat
Cons:
- Understanding the technical aspects of VPN is a necessity

TunnelBear
BOTTOM LINE: TunnelBear is demographically one of the most accessible VPNs around. Although routers, game consoles, and torrenting won’t work with TunnelBear, this is the easy choice for anyone who has limited technical expertise and wants the best “download and go” experience.
Pros:
- Simple and accessible in about all aspects of setup and function
- Great, easy-to-navigate UI
- Bonus points: It contains some of the best bear art on the internet
Cons:
- Highly restricted in technical aspects like protocol, encryption, and compatibility
- Caused a noticeable performance loss in our testing environment

CactusVPN
BOTTOM LINE: This is a great option when price takes precedence over features or fluff. CactusVPN has all the necessities of a VPN packaged together in a simple UI, all for under half of what most commercial products charge. The trade-off, though, is in flexibility; users have limited selection in servers and locations.
Pros:
- Easy-to-use UI
- Cost-effective, running only $4.99 a month
Cons:
- Limited to three concurrent connections across devices
- Small number of servers (4-7 depending on plan, with more available on their $6.99 option)
Each of these VPNs ensured privacy, performed well, and will prevent your ISP from gathering information about your web traffic (the desired outcome).
Methodology
For starters, our testing environment was a Virtual Machine running 64-bit Windows 7. Using VMware, we created several snapshots each with only the default Windows settings and the installation of one of the VPNs. From there, we set out to test our VPNs on three factors: privacy, performance, and ease of use.
Privacy
First, we set up Wireshark for our host machine to listen on our Virtual Network interface. Because all traffic from our VM must be routed through our host before leaving our network, we could effectively monitor whether the data passing through was properly encrypted. Leveraging this, we generated several types of traffic and analyzed it for plaintext content or IP destinations that didn’t match the VPNs (since all traffic should go through the VPN).
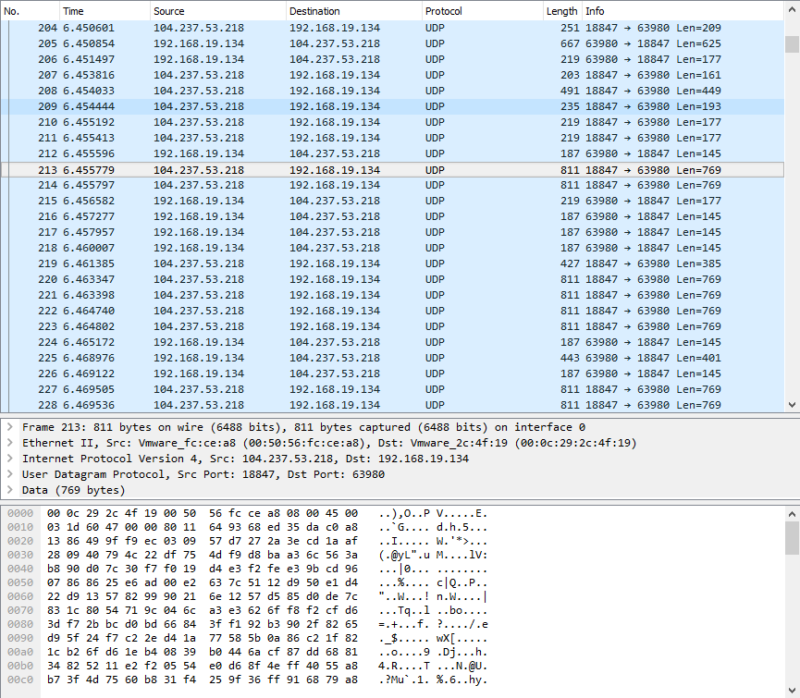
After confirming the VPNs encrypted our traffic properly, we looked at the different protocols and encryption methods they supported. Out of the five we selected, all of them support AES-256 encryption and most support a common subset of protocols (OpenVPN UDP/TCP, L2TP, PPTP, and SSTP).
The last step in our privacy check was to connect dozens of times to the same server and judge the range of IPs we can receive. We recorded whether it changed every time, occasionally repeated, or always repeated. At that point, we took a step back from the technical detail and looked for what methods of secure payment each provider offered – could you purchase your VPN with Bitcoins? Gift cards?
For those who value total anonymity, here are our results:
- PureVPN: Both Bitcoins and gift cards are supported as secure payments
- TorGuard: Both Bitcoins and gift cards are supported as secure payments
- ExpressVPN: Bitcoin payments are supported
- CactusVPN: Bitcoin payments are supported
- TunnelBear: Bitcoin payments are supported
Performance
We started to analyze how well the VPNs held up in terms of speed, stability, and overall technical aptitude. The first phase of this portion of testing was running a speed test. We conducted five back-to-back speed tests using speedof.me for each VPN, allowing each VPN to choose their own recommended server with OpenVPN as the protocol. We then averaged the results, recorded them, and compared against the average speed taken without any VPN.
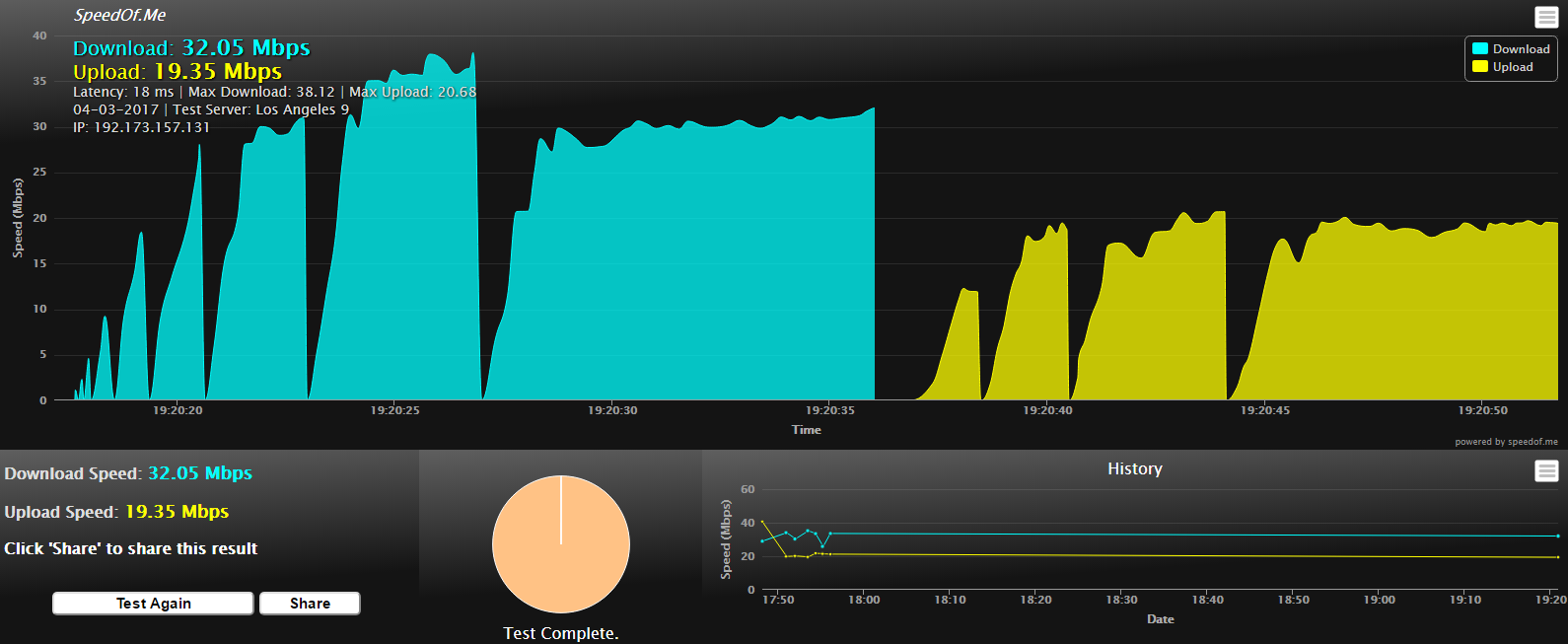
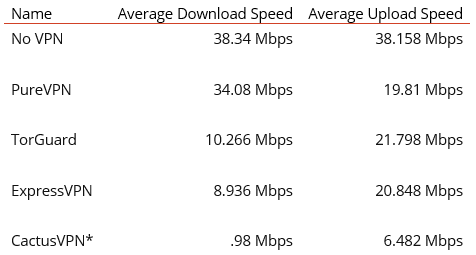
Figure 3 - A More Granular Look at the VPN Speeds We Measured
*Our CactusVPN subscription was chosen to maximize server count, forcing tests with extremely distant European servers.
Ultimately, this step revealed that PureVPN vastly outperforms the other four choices in our testing environment.
Finally, we tested each VPN’s performance to check if it failed open or closed. These terms mean figuring out if each VPN, when forced to crash unexpectedly, maintains the encrypted connection or drops it. So, after terminating the process of each of our choices in the middle of a stable connection, it was determined that only TorGuard did not maintain an encrypted connection (or kill the connection entirely).
Ease of Use
The most subjective metric we examined was how easy it was to install and use each VPN. Ease of use is a very important selling point for companies offering encrypted connections. Our general process involved navigating through the UI, establishing a connection, and determining the difficulty of the configuration settings. We also reviewed which devices were supported for each VPN, and what options were available for receiving online support. Most of that data that can be gathered for ease of use can be found in our Pros and Cons chart above.
One more thing: Each VPN we tested provides users with a mobile app for Android and iOS. These applications will install the VPN certificate onto the device automatically, making configuration and use of a VPN on a mobile device incredibly easy.
Other VPNs We Tested
Before we leave you, here are the VPNs that didn’t make the cut as well as the reasons why they were left on the sidelines.
HideMyAss:
- Failed to establish any connections in our testing environment, thus making it impossible to test
VyprVPN
- Establishing a connection was extremely slow
- Lacks any out-of-the-ordinary features
IPVanish
- Hard to navigate UI
- Installation in our testing environment required reaching out to other help sites in search of TAP drivers when initial installation failed
Trickbyte
- Fairly expensive ($15) for a VPN that just uses the windows settings for a connection
- Lacks a client
- Setup requires strict adherence to a how-to guide on their website
StrongVPN
- Abandoned after frequent crashes and errors in our testing environment
Coming Soon
This is the only beginning of our journey into VPNs. We will be following up with related posts in the coming weeks. Stay tuned!
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.
Recommended Posts
You might be interested in these related posts.

Apr 02, 2024
Technology and Software: 2023 Insights From the Ponemon Institute

Apr 01, 2024
Practical Measures for AI and LLM Security: Securing the Future for Enterprises

Mar 12, 2024
Implementing the FDA's 2023 Requirements for Medical Device Cybersecurity

Feb 28, 2024
Unlocking Job Opportunities with LinkedIn and Artificial Intelligence