
Patch Date
April 10, 2017
Reported Date
February 7, 2017
Vendor
SolarWinds
Systems Affected
SolarWinds Log & Event Manager (LEM) before 6.3.1 Hotfix 4
Summary
An improper access control vulnerability was discovered in the SolarWinds’ Log & Event Manager (LEM) management console (CMC). The CMC is a restricted environment providing functionality for upgrading or maintaining LEM appliances. This vulnerability allows an authenticated user to bypass restrictions imposed by the CMC and browse the underlying server’s filesystem, as well as read the contents of arbitrary files contained within.
Vendor Status
The vendor has been notified and has issued patches.
Exploit Availability
To demonstrate the impact of this vulnerability, the assessment team browsed the filesystem of the SolarWinds appliance to locate and then read the file containing the admin user’s password hash.
By running the editbanner command in the LEM CLI, a nano session was opened, as shown below:
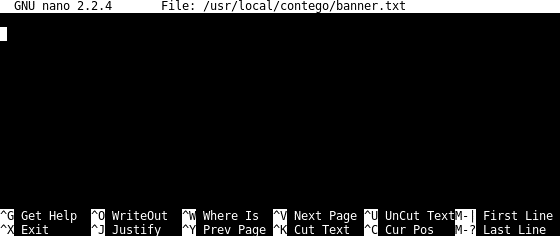
Although not displayed, the key bindings to read a file (^R), or to open the filesystem browser (^R, ^T) were still available, and using them resulted in the following display:
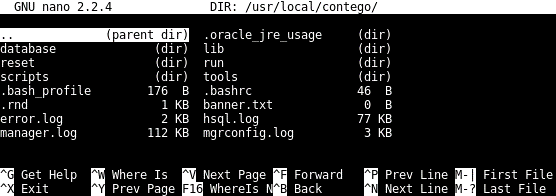
Figure 2 - Browsing SolarWinds server's filesystem in nano text editor
After navigating to the directory /usr/local/contego/run/manager, the file UserContextLibrary.xml was selected. Its contents, which included the administrative user’s password hash, were dumped into nano’s buffer:
/usr/local/contego/run/manager/UserContextLibrary.xml
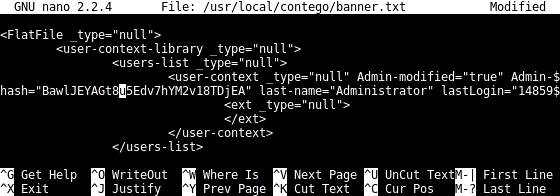
Figure 3 - Administrative user's hash visible from nano editor
This proof of concept demonstrated that it is possible to escape the access controls implemented by the SolarWinds LEM CLI and the installed nano text editor to browse the underlying filesystem and read arbitrary files.
Researcher
Baker Hamilton, MD, MMSc of Bishop Fox
For Reference
- CWE-284: Improper Access Control
- CVE - CVE-2017-7646
- LEM V6.3.1 HOT FIX 4 IS NOW AVAILABLE
The team at Bishop Fox would like to thank SolarWinds for their cooperation in quickly resolving this matter!
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


